
For a long time now, certificate authorities have been the go-to spot for anyone that needs a suitable SSL certificate like standard SSL, code signing certificate, EV SSL or any other type to secure their website and a code signing certificate to authenticate the software/application. They have indeed helped a great deal to secure web communication and ensure the integrity and confidentiality of information being shared online. However, all that glitters is not gold, and we have had sensitive cases in the recent past where the power and effectiveness of certificate authorities have come under scrutiny.
For instance, Dutch CA DigiNotar found themselves in hot soup in 2011 when an intruder penetrated their network and issued themselves a valid certificate for the domain google.com. Comodo has also suffered such blows where fraudulent certificates for domains owned by Yahoo, Skype, and Google have been issued.

(Image Courtesy: https://www.venafi.com/blog/need-for-certificate-transparency )
It is for such reasons that Google came up with the Certificate Transparency (CT) project in 2013. This is not an aim to diminish the existing system where certificate authorities issue X:509 certificates to endorse a server’s claim to its public key. Usually, the SSL/TLS protocol works through Public Key Infrastructure (PKI) where there is a private key attached to the server and a public key that the server issues to the client browser.
However, there are many loopholes in that most browsers come preconfigured with a list of approved CAs that they trust with issuing legitimate certificates. Now if an intruder managed to bind a fake public key to a domain by issuing themselves a valid certificate fraudulently, this might easily go unnoticed for a long time.
The Certificate Transparency project proposes reinforcing the existing X-509 validation system with publicly-auditable logs. Public logs are high availability servers meant to maintain append-only databases of certificates issued by CAS.
This public log will come in handy in providing proof of a certificate’s presence in the log database which clients can check during a Transport Layer Security (TLS) handshake. There will be special entities known as auditors and monitors whose job will be fetching proofs of existence and consistency of certificates for clients in the hash tree of logs.
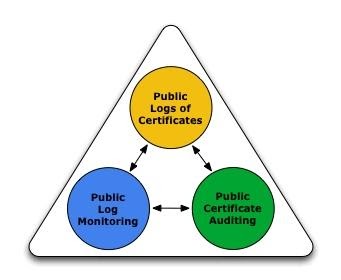
(Image Courtesy: http://www.certificate-transparency.org/what-is-ct )
Certificate Transparency is indeed a brilliant idea that seeks to have web clients not accept certificates unless they are publicly logged. This will make it impossible for a certificate authority to issue a certificate for a domain unless it’s publicly visible.
This, in turn, will easily expose CA misbehaviour like when the append-only property is disregarded or when the log shows a different set of certificates to different clients at any given point. Ideally, the public log listing should be consistent all around the world.
It is this great need for the consistency of logs that has brought the suggestion of blockchain technology to the table. This is a fast-rising technology that is reputed for operating distributed applications.
A blockchain can be defined as a sophisticated ledger of recording transactions that is maintained within a distributed network of peers that are mutually untrusting. Every peer will keep a copy of the ledger, and all the multiple ledgers will be checked for consistency in a process known as consensus.
Namecoin blockchain is a great choice in serving this purpose. It’s among the very first forks of Bitcoin that was created to provide a better DNS-like system that would use blockchain instead of DNS root servers to map domain names to DNS records. The incredible existing properties of Namecoin make it ideal to be used as a Public Key Infrastructure.
The Ethereum blockchain is another excellent idea that has been tested and tried with extending standard Transport Layer Security architecture. The findings have identified the Ethereum network as a perfect bet for detecting, making public, and responding to any CA misbehaviour.
The incredible role that certificate authorities play in ensuring the authenticity, integrity, and confidentiality of information being shared online cannot be downplayed. CAS is responsible for much of the safe browsing that we witness in our day to day operations.
However, to err is human and even the magnificent Titanic had its shortcomings. What we can do to fix the few errors that might result from the CA-issued X-509 certificates is to augment that process with better technology like blockchain using public logs. That way you will still get your SSL certificate from a CA, but now the availability of public logs will keep all fakes at bay.
Disclaimer: This is a paid article. KryptoMoney does not endorse and is not responsible for or liable for any content, accuracy, quality, advertising, products, or other materials on this page. Readers should do their own research before taking any actions related to the company. KryptoMoney is not responsible, directly or indirectly, for any damage or loss caused or alleged to be caused by or in connection with the use of or reliance on any content, goods or services mentioned in the article.
Keep in mind that we may receive commissions when you click our links and make purchases. However, this does not impact our reviews and comparisons. We try our best to keep things fair and balanced, in order to help you make the best choice for you.