
First things first, Google 2FA or Two-Factor Authentication is a product by google which offers you an additional layer of security on your various web accounts on different websites including cryptocurrency exchanges. Before I explain you “What is Google 2FA”, let us first understand “What is Two-Factor Authentication and Why Do We Need It”.
Two-Factor Authentication (2FA) is simply another layer of protection to your web accounts. It is like an additional password which is required to successfully log-in after punching in the original password along with the username.
Imagine that you hold a security locker with your bank and store all the valuables there. You can access the same through the keys provided by the bank. However, a combination of two keys is required to open the locker, one belonging to the customer and another to the bank. Here, the key required by the bank is like 2FA.
The 2FA password is not the same and a new password or code is generated everytime. Infact Google 2FA changes every thirty seconds.
The security of crypto assets stand as the biggest threat to crypto market shadowing the likes of volatility and comprehensive regulation. Although the fast learners have shifted base to “hardware wallets such as Ledger Nano S for storing the same in a secured fashion, a lion’s share of crypto holders are still relying on cryptocurrency exchanges for maintaining their holdings. Although, this is not the best practice and neither it is recommended, it surely is the most suitable option since it is almost impossible to set up an individual wallet for all the new tokens. But there are ways to protect your crypto exchanges account and prevent log-in from unidentified sources by using “Google 2FA”
The crypto news radar is bubbling with sightings of more and more exchanges pulling their shutters down. But a bigger fear is looming over the horizon in the shape of funds being hacked from the exchanges due to bad security practices and personal negligence. Chainalysis has reported that Ethereum worth $225 million has been stolen by cyber-criminals in 2017 through website phishing in which a spoof website is created looking exactly like the original. A recent case was witnessed when hackers tried to hack Binance cryptocurrency exchange, although they were not successful.
Bloomberg has recently revealed that there lies a 1/10th chance of ending up as a victim of crypto fraud while engaging in ICOs. Taking into account all these points, it is imperative to deal with cryptos in a diligent manner by giving top priority to cybersecurity. This is exactly where Google 2FA or Two-factor Authentication comes in to fill the void by adding an extra layer of security to your trading portal.
Although it seems extremely daunting, cybercriminals are coming up with newer ways of hacking into your account with each passing day.Google 2FA can put an end to such malice by sealing the access route of unauthorised users in spite of being in possession of the requisite credentials.
This procedure is completed by ensuring that the login setups involve something of exclusive nature. The following factors are generally coupled with credentials for coming up with a viable two-factor authentication:
The implementation process of two factor authentications might vary from company to company.
The operation of two-factor authentication process is almost similar to the existing login procedure with the only difference lying in the requirement for an additional piece of information which has to be filled in along with the user ID and password. One Time Password (OTP) sent on the registered mobile number or email address can be used for intimating this additional information. It can also take the shape of a code on an application such as the Authy or Google Authenticator which needs to be entered in the login page of the website along with the credentials.
Ideally it is not recommended to use your phone or email for authentication as the same can be easily hacked by the cyber criminals. However, you can establish complete control over the security paired with a mobile app which is used for generating new password each time. Now, let me explain you “What of Google 2FA?”

Google 2FA or Two-Factor Authenticator is a software token that implements two-step verification services using the Time-based One-time Password Algorithm (TOTP) and HMAC-based One-time Password Algorithm (HOTP), for authenticating users of mobile applications by Google. It is simply a mobile app which needs to be paired/synced with your web account.
You have to first pair the google 2fa mobile app with the website you want to secure.
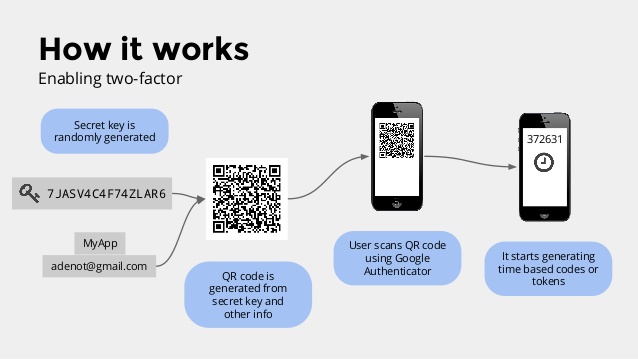
Pairing simply involves scanning a barcode which is displayed on the website by the google 2fa mobile app. Within few milli-seconds after scanning, the google 2fa code is generated on your mobile. (Remember, while scanning the barcode, a secret key is also mentioned on the same screen. Do note that secret key or simply take a screenshot of that screen. It is used in case you have lost or damaged your mobile phone).
Pairing is not a tough job and anyone can pair it within 2 minutes. Just follow the instructions mentioned.
After pairing and when you try to log-in next time, you have to enter the code running on the google 2fa mobile app after entering your username and password. The code changes every thirty seconds and hence it improves the security measures.
As mentioned above, 2fa or two factor authentication adds an extra layer of security. Most users have only single layer of protection i.e their password. With 2fa installed, if a hacker by chance gets access to you password, he/she still needs the 2fa code running on your mobile which changes every thirty second.
With two-factor authentication, you’ll protect your account with something you know (your password) and something only you have (your phone or Security Key).
Your trading account can benefit from a secondary security layer courtesy the 2FA. Thus, in spite of your trading company falling prey to data theft, the hackers won’t be able to access your system although they are in possession of a username and password. Since hackers cannot access your email ID or phone with equal ease, 2FA is perfect for users who wish to enhance their account’s security. This feature maintains its stronghold even in the case of a Brute Force attack where hi-tech software is used for breaking into the security parameter and reveal the account’s login credentials. And if you use 2FA mobile app, which generates a new password every 30-45 seconds, it’s next to impossible for hackers to hack into your account untill and unless they don’t have your smartphone.
The increasing threats of cyber-attacks taking shape around the world has added inertia to the recognition and development of cybersecurity at corporate level. This in turn is instigating organisations to take a critical approach for handling the same by adoption of best security parameters existent in the virtual world. However, these approaches might not always be easy on one’s pocket. 2FA enters the cybersecurity arena as an easy, simple and efficient way for organisations to cater to their security issues. This is increasingly relevant for start-ups and SMEs who are always on the search for cost-effective solutions.
Now it is not necessary for employees and management to be in a secure office environment for accessing sensitive data given the increased sense of security. The same is accessed through two-factor authentication on the go which acts as a buffer for mobile technologies. Employees can access documents, data, presentations, worksheets as well as remote location or virtual devices without jeopardizing the inviolability of the sensitive information. You can refer to the example of an employee who logs in to the company portal by using his personal tablet. No other family member can gain access to this information while using the tablet later on since 2FA makes it simply impossible to log in to the system in spite of having knowledge of the requisite credentials.
It often becomes difficult for companies to handle customer queries arising out of login issues. This is a core area which needs to be automated since it takes up a considerable amount of the account and help-desk manager’s time. Two-factor authentication can serve as a staple solution to this inefficiency by allowing users to reset their passwords in a secure manner based on the combination of the chosen authentication factor and personal email id. This can also stop hackers from abusing the system and gaining unauthorised access by resetting the account password time and again.
Identity theft stands as one of the biggest problems plaguing the first world population. It was revealed by the Identity Fraud Study of 2017 that a whopping $16 billion was stolen in US alone from 15.4 million customers during 2016 hence accounting for a heart-stopping $107 billion in the last six consecutive fiscals. The main reason behind this is the unauthorised access gained by hackers over our account and all other linked accounts which can cause sensitive details to suffer. Thus, if your crypto trading account gets hacked today, your bank account information and KYC details will also stand at a heightened risk of being compromised.
Modern day hardware wallets such as YubiKey work in perfect sync with such two-factor authentication modes. Mobile Applications such as Authy and Google 2FA are also increasing in popularity amongst the millennial population. These app bases 2FA are used when you transact over “crypto exchanges such as Bittrex, Poloniex,Binance etc.
The hardware authentication device of YubiKey comes stacked with an array of features such as:
This device can also be used in websites which do not support OTPs by seeking help of stored static passwords. The fact that this device is used by both Goggle and Facebook for storing the employee credentials stand as a proof of its authenticity.
Authy and Google Authenticator adds a string of websites or accounts where 2FA can be used via an easy to use interface and optimum swiftness for hassle-free login. Under Authy, it is mandatory to provide both the phone number along with the email ID. A verification pin is sent to the registered phone number while the account is initially set up. Authy also delivers multi-device support which can be of great help in de-authorizing the device and safeguarding the data on the possible case of a device loss. All the previous 2FA privileges can be taken away immediately from your lost or stolen device and a new one can be authorized for accessing all your accounts immediately.
I am sure that by now you must have understood each and everything about two-factor authentication. 2FA is not an additional feature now but a necessity in order to protect your funds on online websites or even you other web accounts. As cybercrime is picking up day by day, one must be stupid enough to not to use two factor authentication. Just one thing i mention again is that whenever you are installing the google 2fa, do note the security key while scanning the barcode or simple take the screenshot of that screen where in the barcode and security key, both are together.
In case if you still have any doubts, feel free to ask in comments section below,
KryptoMoney.com publishes latest news and updates about Bitcoin, Blockchain Technology ,Cryptocurrencies and upcoming ICO’s.

Rohit Kukreja
Rohit Kukreja is a Commerce graduate with Financial Markets expertise involving Stocks, Forex, Futures & Options Market and now Bitcoins & Cryptocurrency Markets. Blockchain Enthusiast but not a techie, Rohit is an active member of various Blockchain & Crypto communities all over India.
Keep in mind that we may receive commissions when you click our links and make purchases. However, this does not impact our reviews and comparisons. We try our best to keep things fair and balanced, in order to help you make the best choice for you.